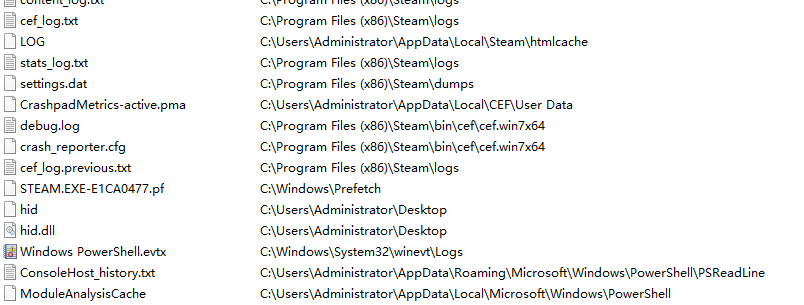
输入链接,在everything中监听
打开链接,释放了hid和hid.dll样本报告-微步在线云沙箱 (threatbook.com)
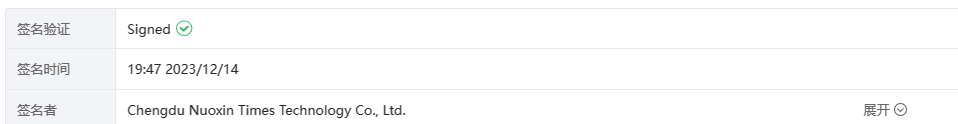
分析了下签名,怀疑惯犯
近期 Higaisa(黑格莎) APT 针对中国用户的钓鱼网站、样本分析(一) | CTF导航 (ctfiot.com)
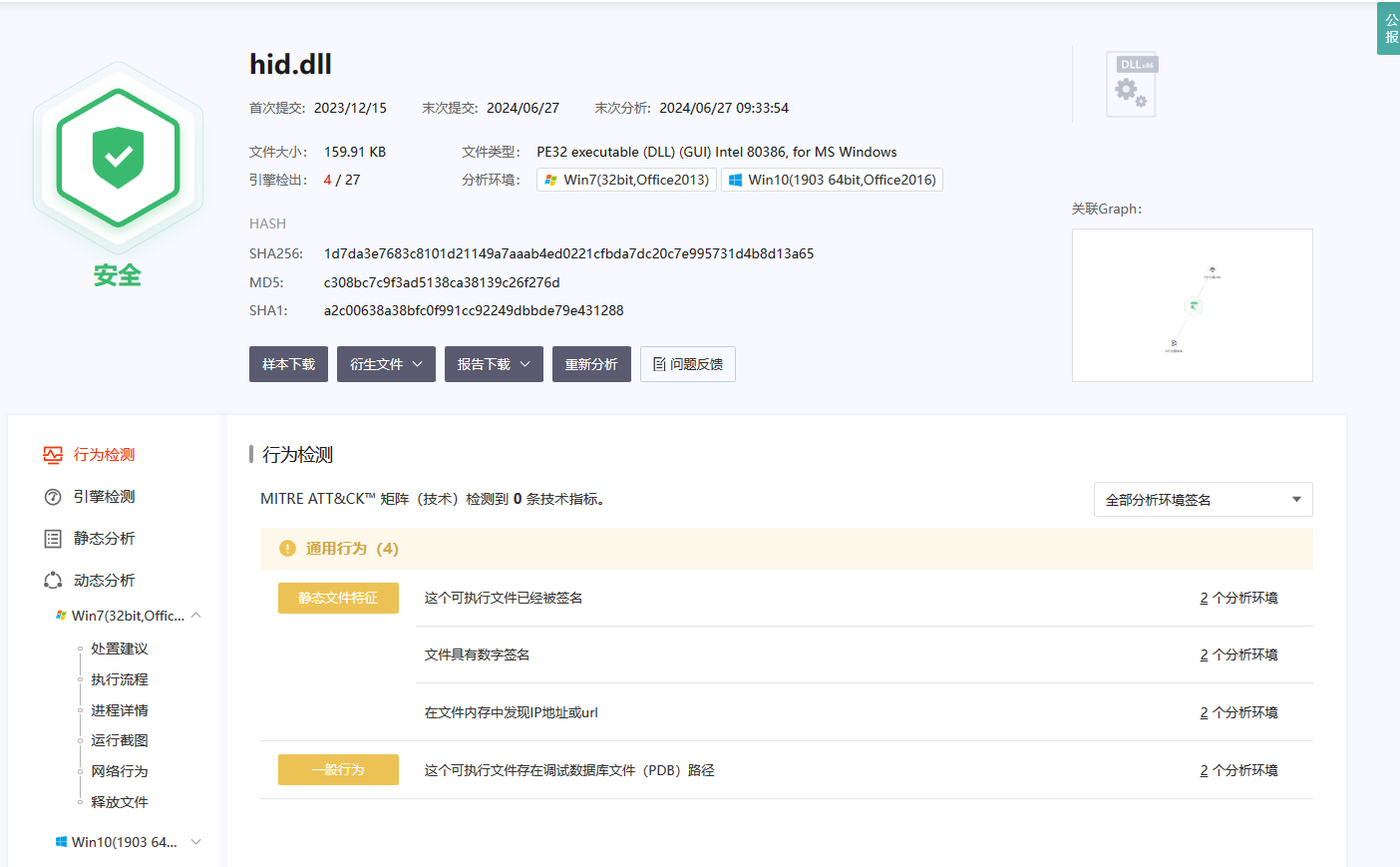
逆向分析hid.dll,拖入ida
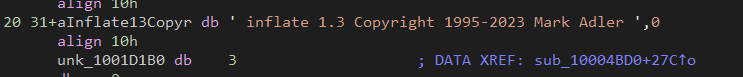
查看字符串,发现
Mark Adler不是那个开发zlib的吗
基本确认了,存在zlib加密,分析hid文件
先写个脚本解密
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 import zlibdef decompress_zlib_file (file_path, output_path ): try : with open (file_path, 'rb' ) as file: compressed_data = file.read() decompressed_data = zlib.decompress(compressed_data) with open (output_path, 'wb' ) as output_file: output_file.write(decompressed_data) print (f"Decompressed data written to {output_path} " ) return True except (zlib.error, IOError) as e: print (f"Error decompressing file: {e} " ) return False input_file_path = r"C:\Users\23038\Desktop\hid.zlib" output_file_path = r"C:\Users\23038\Desktop\decompressed_pe.dll" success = decompress_zlib_file(input_file_path, output_file_path) if success: print ("Decompression and file writing successful." ) else : print ("Failed to decompress and write the file." )def decompress_zlib_file (file_path, output_path ):
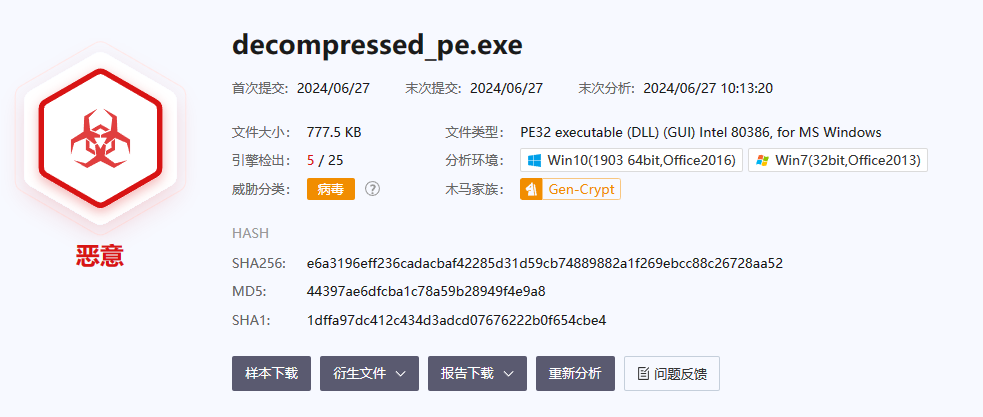
分析decompressed_pe.dll,先拖入沙箱
样本报告-微步在线云沙箱 (threatbook.com)
不出所料,报毒
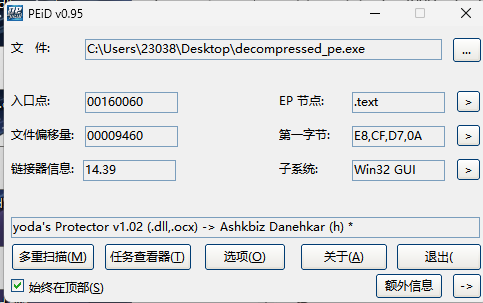
加壳了,exeinfo扫不出来,换peid扫出来
现在很多软件加壳之后,你用查壳软件一查,都显示yoda壳
不知道是什么壳不敢分析了,等考完试找个虚拟机环境看看